Complete Setup: Intune-managed BitLocker — Encrypt Windows & Escrow Keys to Entra ID
- Hanna Korotka
- Sep 3, 2025
- 3 min read

SMBs lose laptops, auditors ask for proof, and help desks need a simple recovery flow. This complete setup shows how to enforce Windows disk encryption via Intune, enable easy key retrieval for recovery, and verify compliance—without piling work on users or IT. With Intune-managed BitLocker, encryption is enforced by policy and recovery is straightforward for both users and administrators.
Prerequisites
A device must meet the following conditions to be eligible for silently enabling BitLocker:
If end users sign in as Administrators, the device must run Windows 10 version 1803 or later, or Windows 11.
If end users sign in as Standard Users, the device must run Windows 10 version 1809 or later, or Windows 11.
The device must be Microsoft Entra joined or Microsoft Entra hybrid joined.
The device must contain TPM 1.2 (or newer).
BIOS mode must be set to Native UEFI only.
Step-by-step deployment
1) Create the disk-encryption policy
Microsoft Intune admin center > Select Devices > Manage devices > Configuration > On the Policies tab, select Create.
Set the following options:
Platform: Windows 10 and later
Profile type: Select Templates > Endpoint protection, and then select Create.
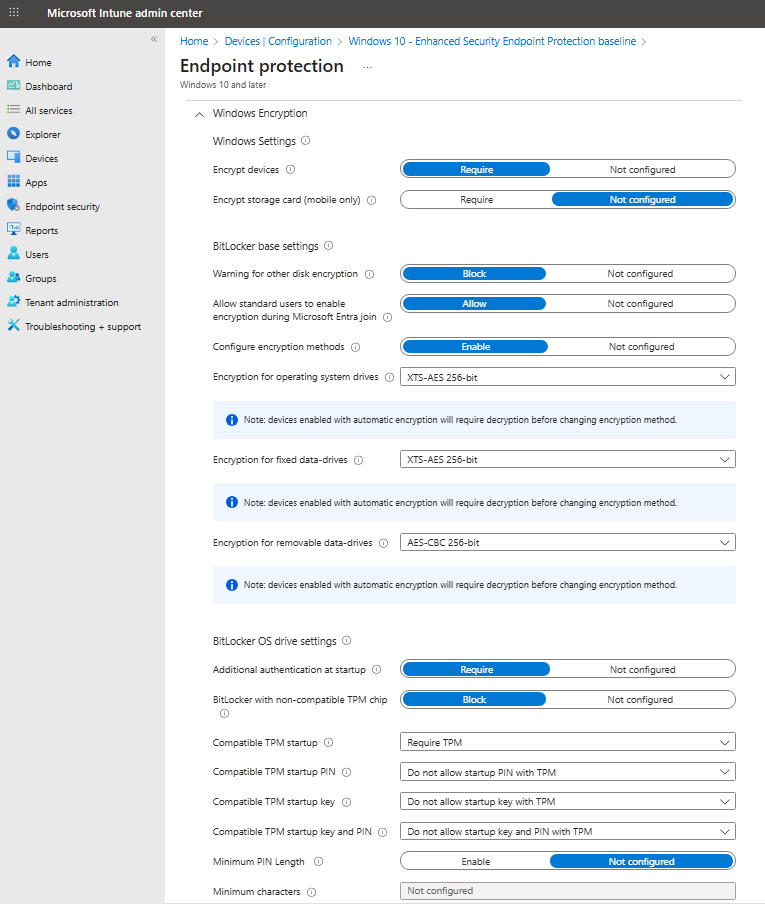
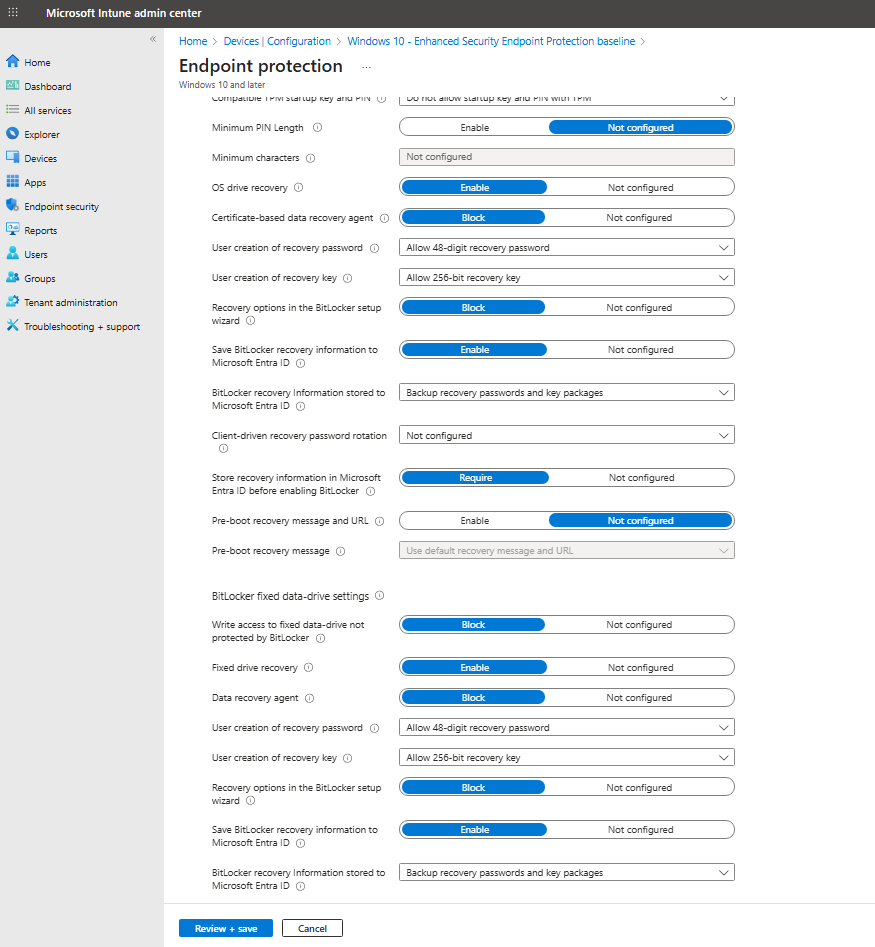
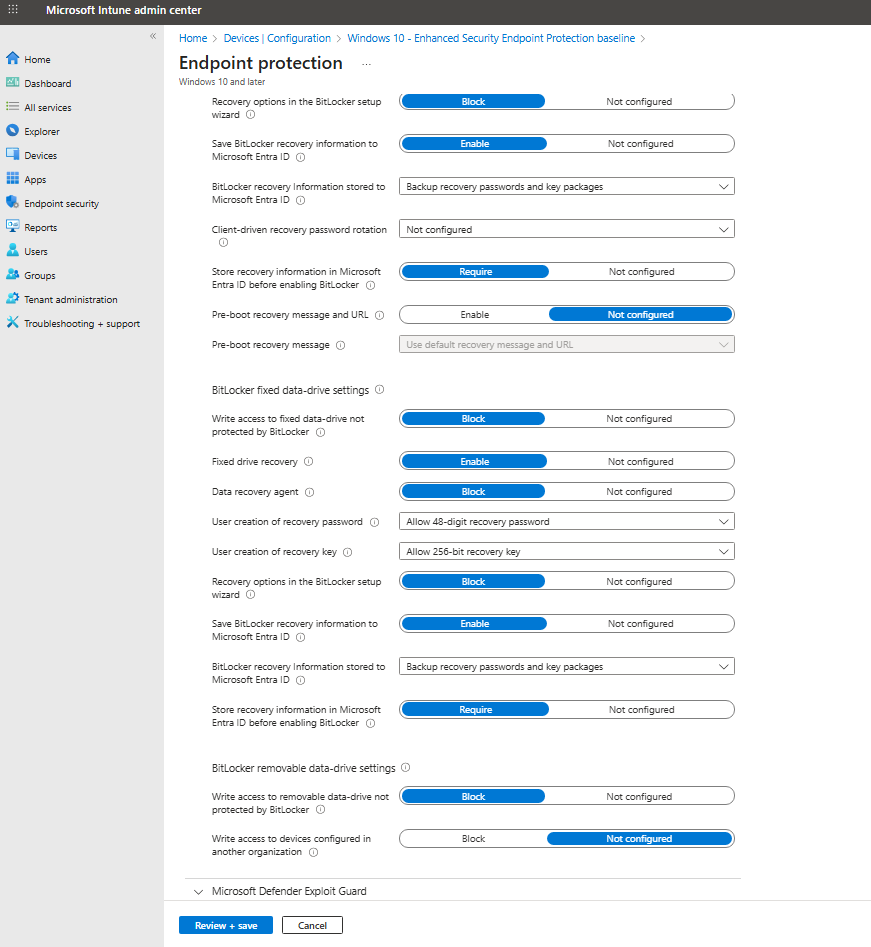
On the Configuration settings page, expand Windows Encryption and configure settings for BitLocker to be silently enabled on devices. (Please see screenshots below.)
Select Next to continue.
Complete configuration of other settings, and then save the profile.
Assign to a pilot dynamic group first (e.g., cloud-joined laptops), then expand.
2) Validate encryption
Use Intune’s Device encryption status report to verify protection.
To find the report: Sign in to the Microsoft Intune admin center. Select Devices > Manage devices > Configuration, select the Monitor tab, and then select Device encryption status.
View BitLocker recovery keys
Several reasons might cause a Windows 10/11 device to go into recovery mode. Once recovery mode is enabled, the user needs to enter BitLocker recovery keys to unlock the encrypted drive of the Windows 10/11 machine managed by Microsoft Intune.
Why devices enter recovery mode (examples): multiple failed sign-in attempts (per your policy), hardware malfunction, unexpected configuration change, or another security event. The BitLocker recovery key is required to ensure only an authorized person can unlock the PC and restore access to encrypted data.
For admin: Access the BitLocker recovery key in the Microsoft Intune admin portal
Sign in to the Microsoft Intune admin portal with your admin account.
In the admin center, select Devices, then All Devices.
Find the specific device.
Select Recovery keys in the device menu.
To display a recovery key for a drive, select Show recovery key.
A pane on the right displays the device information, including the BitLocker recovery key. Select the copy icon to copy the key.
For admin: Access the BitLocker recovery key in the Microsoft Entra admin portal
Sign in to the Microsoft Entra ID admin portal with your admin account.
Go to Identity > Devices > All devices.
Find the specific device.
Under Manage, select BitLocker keys.
To display a recovery key for a drive, select Show recovery key.
A pane on the right displays the device information, including the BitLocker recovery key. Select the copy icon to copy the key.
Why this is the right move for SMBs
Low friction for users; strong coverage for lost/stolen devices
Clear reporting for cyber-insurance and regulatory audits
Simple recovery with immediate key rotation—no risky key reuse
How we can help
As an MSSP focused on Microsoft cloud security for SMBs, we can review device readiness, deploy and validate your encryption policies, streamline recovery procedures for your help desk, and align reporting with audit and insurance needs—so you stay protected without adding operational overhead.